Australia’s latest Annual Cyber Threat Report 2024-2025 delivers a clear message to every board member and organisational leader: cyber threats are evolving and so must our resilience.
Behind the numbers are real-world consequences: business disruption, service outages, and financial loss that ripple through every sector of the economy.
The 2024–25 ASD report paints a stark picture:
- Over 84,700 cybercrime reports were received last year — one every six minutes.
- The ASD Cyber Security Hotline received 42,500 calls, a 16% increase from the previous year, and responded to over 1,200 cyber security incidents (an 11% increase).
- Critical infrastructure organisations were notified 190 times of malicious activity — up 111%.
- The average cost of cybercrime rose to $33,000 for individuals and $80, 850 for businesses.
Industrialised Cybercrime — Scalable, Service-Based, Global
The report confirms what many in the field already recognise: cybercrime has industrialised. Threat actors are becoming increasingly professional— offering “Cybercrime-as-a-Service” infrastructure that scales globally.
Europol’s takedown of SIMCARTEL, a vast SIM farming operation, is a case in point. This wasn’t mere fraud — it was an organised cyber service provider. They offered the infrastructure for phishing and identity theft: SIM boxes, automation tools, and 49 million fake accounts used to harvest credentials and enable scams at industrial scale.
Meanwhile, AI-powered tools are supercharging malicious activity — accelerating credential theft, automating phishing, and evading traditional detection systems. As the ASD warns, AI is now an enabler of malicious cyber activity, not just a target of it.
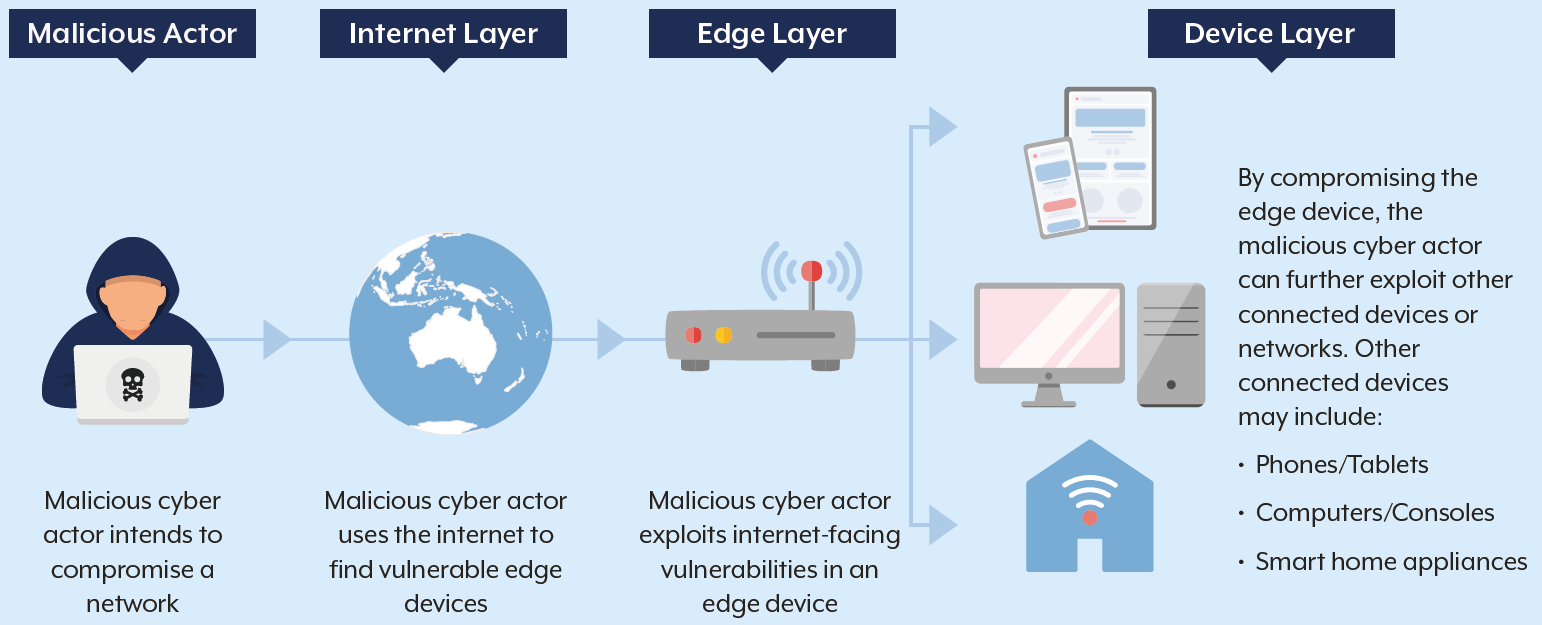
Vulnerable Edge, Stretched Defences
The ASD highlights that attackers are increasingly exploiting edge devices — routers, firewalls, and virtual private network (VPN) products— often the least patched and most exposed systems.
Organisations with limited cybersecurity resources are especially vulnerable, struggling to maintain cyber hygiene, detect early warning signs, and align with frameworks such as the Essential Eight.
State-sponsored actors are also stepping up operations, probing Australian networks for espionage and disruption — particularly within critical infrastructure, defence, Government and their supply chains. The distinction between criminal and nation-state activity is blurring, amplifying the strategic risk for every organisation.
Four Moves Every Board Should Be Driving
The ASD outlines four key focus areas that define the next phase of resilience:
- Implement best-practice logging — visibility remains the foundation of detection and response.
- Replace legacy systems — outdated technology continues to expose entire networks.
- Manage third-party risk — supply chain vulnerabilities remain a critical blind spot.
- Prepare for post-quantum cryptography — future-proof encryption and data protection.
These aren’t just technical tasks — they are strategic imperatives that demand leadership, governance, and budget ownership at the board level.
Designing for Resilience
So, what can we do? We build resilience deliberately — by design, not by reaction.
- Design for resilience: Segment networks, apply least-privilege access, and monitor for anomalies.
- Secure the basics: Patch systems promptly, harden edge devices, and retire legacy tech.
- Strengthen identity: Use phishing-resistant MFA and enforce strong credential policies.
- Detect early: Enable comprehensive logging and regularly test your incident response plan.
- Backup critical data: Maintain reliable, tested backups to recover from ransomware or destructive attacks.
- Repeat and improve: Cyber hygiene isn’t a project — it’s a culture.
Security Beyond Awareness Month
As Cyber Security Awareness Month closes, it's worth remembering:
Cyber threats don’t follow calendars.
They don’t pause for campaigns or wait for the right moment.
Security must be embedded into culture, processes, and daily decisions.
Every week needs cyber hygiene.
Every day requires vigilance.


.jpg)





